In this day and age most of our lives are happening on the internet: here we shop, we meet our friends and store our precious family pictures. Our personal data, money and memories are always at risk of being accessed by hackers. Talking about cyber security isn't your usual dinner table discussion, so I decided to summarize all the most common threats and tactics in a single post. Don't worry, be aware!
In the cyber security world for enterprise (these are your usual organisations running the internet services you use) we strive to identify the tactics and attacker behaviour. You can read more about them here: attack.mitre.org.
I'll summarize all of them below. Most of the tactics resolve around getting access to the system by escalating priviledges, acquiring your data, running scripts in your system or exploiting your network.
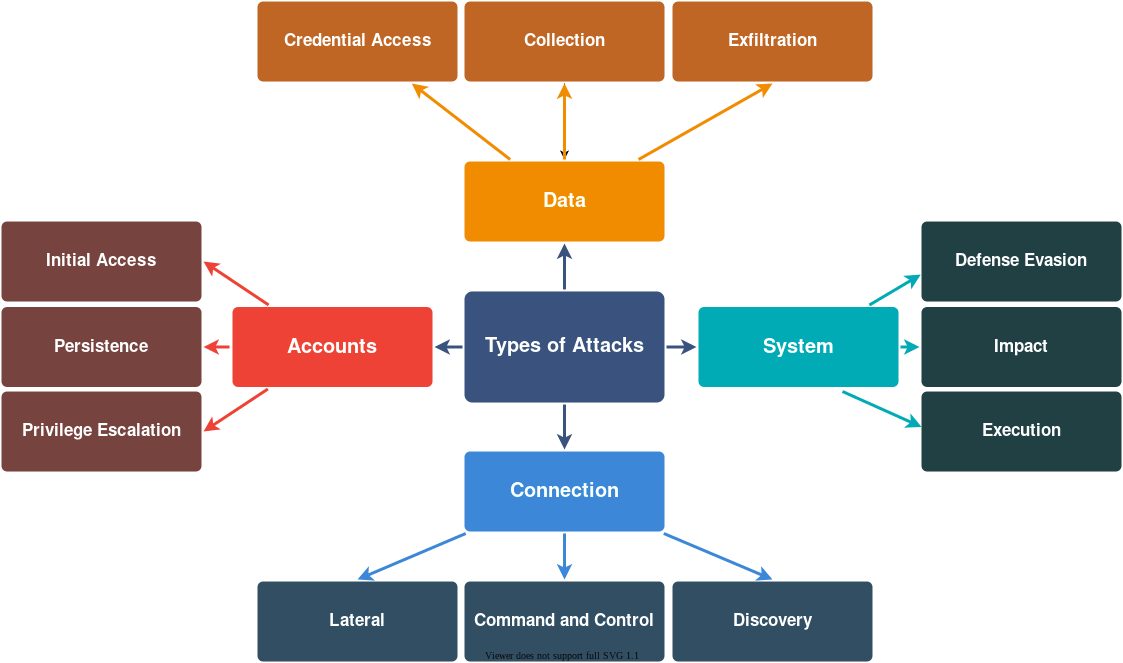
Accounts
We access all of the services as users. Some users have superpowers and can access all the important data and actions on the system - these are admins or priviledged users. Gaining intial access can happen through unsecure WiFi, leaked or guessed password. If hacker can manage to elevate priviledges, they can get hold of your whole system! Persistence means that access to your account can be gained in many ways: through a script injected into the system on boot, through a browser plugin, remote service, etc.
Prevention!
Maintain a list of user prviledges, use least priviledge principle: give out priviledges only if necessary. Make sure accesses are given only for those users who absolutely need the files or that part of the system.
Data
One of the most common goals of hackers is to snatch your data - all the value on your system. They will try to capture your inputs, to get in the middle of your customer and your system to collect the passwords and messages. Sniff your networks to access your user credentials. After collection the data is processed with exfiltration in order to make sense of it.
Prevention!
Choose safe passwords, encrypt your data and monitor your network. Sudden IP address change can warn you that somebody is trying to use a hijacked account.
System
Hackers will try to get around your defences by modifying permissions, using proxies and obscuring themselves. Some hackers, the impact seekers, will try to destroy your service and can go far in deleting data and bringing down the service. They can execute scripts in your system in a timely manner, exploiting your system seemingly unnoticed.
Prevention!
Monitor and track who is accessing your system and where from. Check the blacklists for malicious IP addresses.
Connection
Connection to your system is hackers gateway to exploiting it. They will try to use everything: remote connections, proxies, USB devices, cloud service features.
Prevention!
Try to avoid the use of unecessary USB devices, know your network structure, maintain a firewall. Don't establish unnecessary connections, remove them if they are no longer needed. Last, but not least, know your cloud provider very well to ensure your cloud security!
I hope this was a good overview of all the nasty things that can happen. Gladly, we have the preventive measures for all of them. Healthy monitoring and good habits can go far in the quest of safe internet!
Let the good times roll!